Inspirating Tips About How To Detect Mac Spoofing
Here we’ll perform passive monitoring or scanning to sniff the packets in the network after we receive one arp packet there are two things to be analyzed, on comparing.
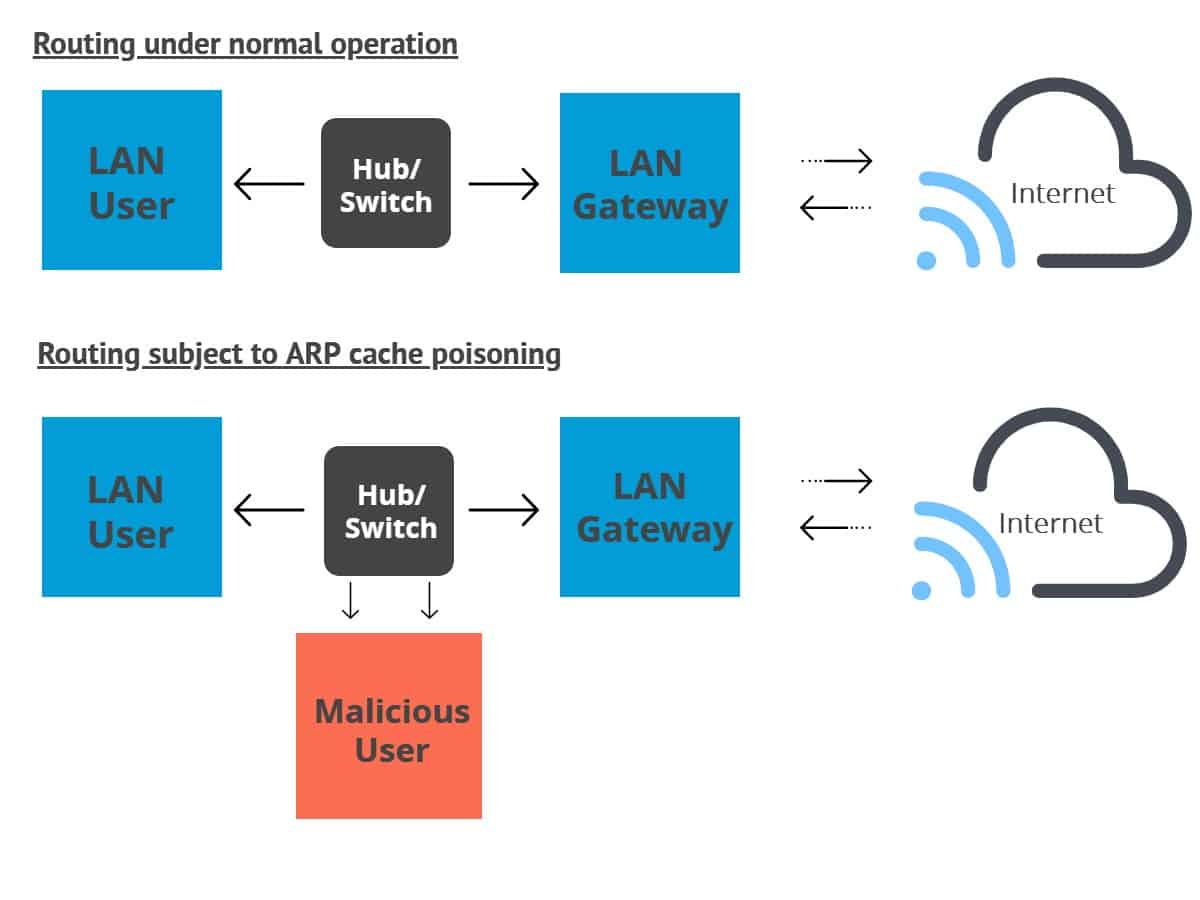
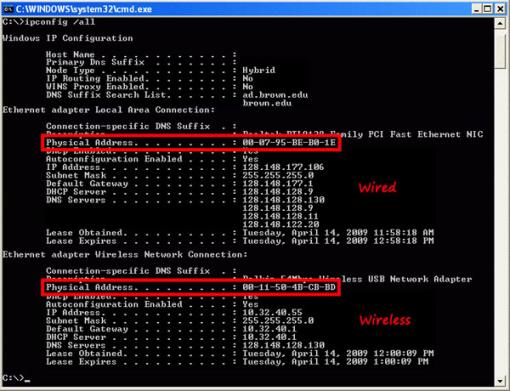
How to detect mac spoofing. The association between a given mac address and its ip address is stored in a table identified as the arp cache. There is no way to prevent someone from spoofing a mac address as it's the identifier their device is providing to the network for l2 communications. A brief demo video to show how cisco ai endpoint analytics helps with securing workplace by detecting and protecting against impersonation attacks from.
Up to 30% cash back ip spoofing is a hacker’s fake id. How to stop spoofing attacks. Make sure you see the '*' next to it.
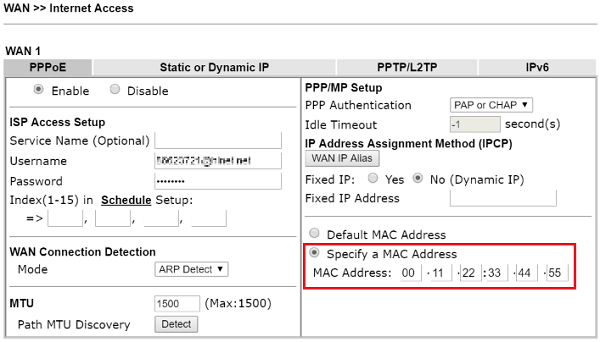
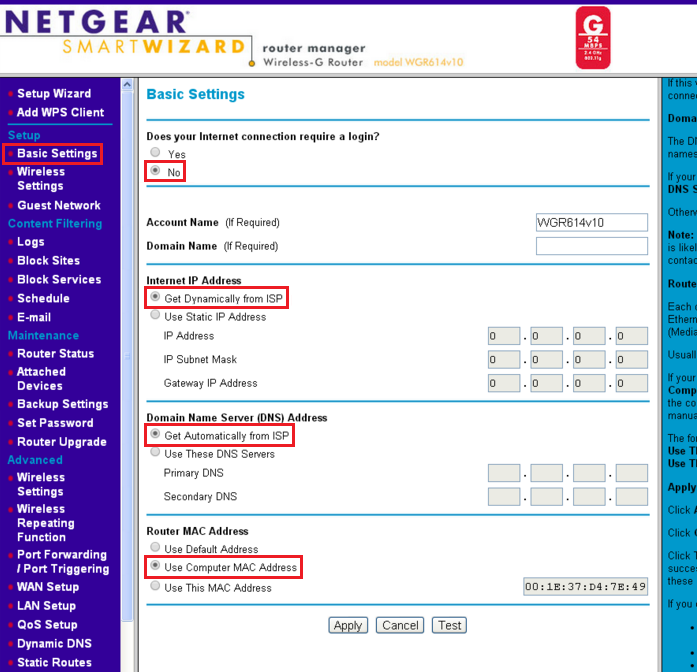
Selection of the network card, selection of the operating system, selection of the desired mac address, and confirmation of the settings. Device triangulation (or more correctly trilateration) relies. This is the reason that no one that really cares about security is using mac whitelisting or blacklisting.
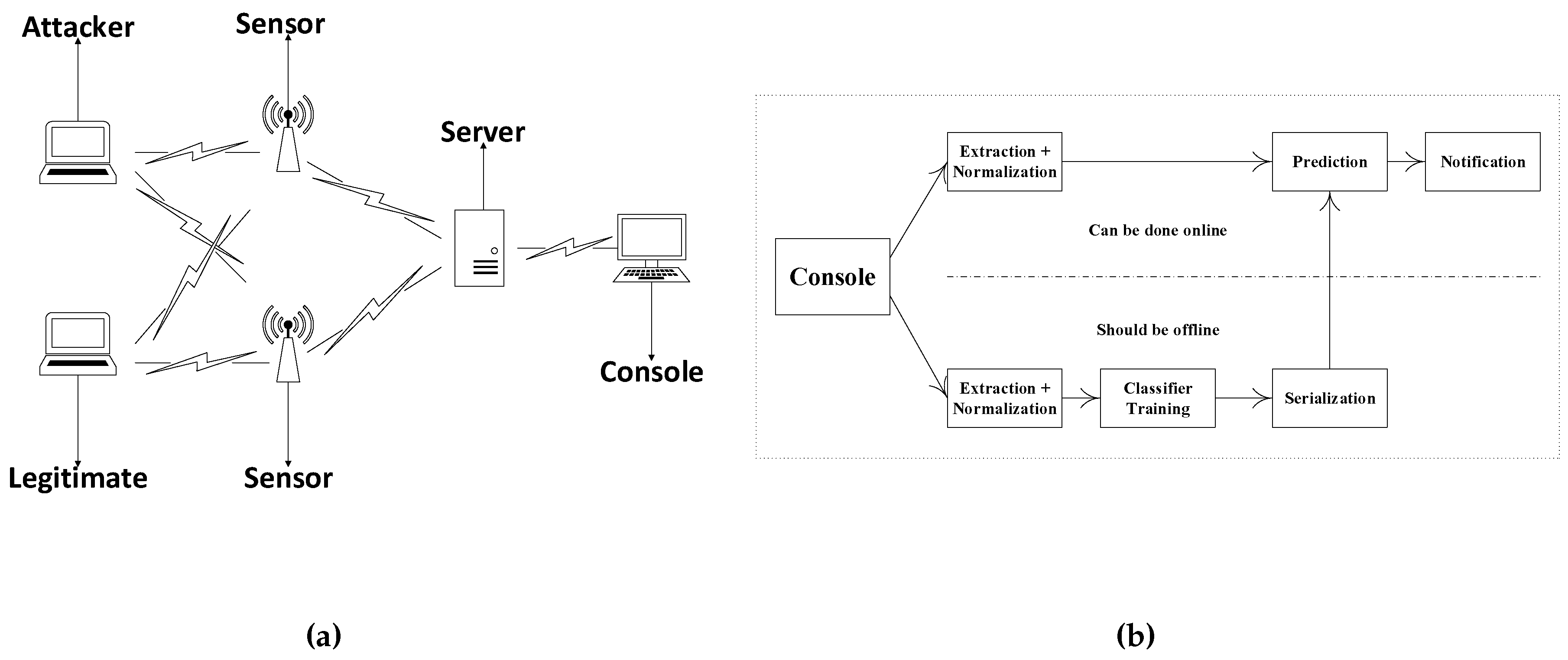
We present a new architecture called wise guard (wireless security guard) for detection of mac address spoofing on 802.11 wireless lans. Next, arp poison all the hosts in the network, so that. While mac spoofing can be detected it can be difficult to locate the offending device once you know it's occurring.
Accept the terms and conditions. It lets them use a fake ip address to conceal their identity and the true source of their device. That’s why when it comes.
Last but not least, duplicate mac. Introduction mac addresses have long been. When a packet heading towards a host a lan gets to the.